The Invisible Value Paradox: Why SMBs Say 'No' to Security
by Velosent Team
Key Takeaways
- The Tangibility Bias is the main reason customers prefer tangible products over invisible security services
- "Show Don't Tell" significantly increases close rates: Visual proof overcomes psychological barriers
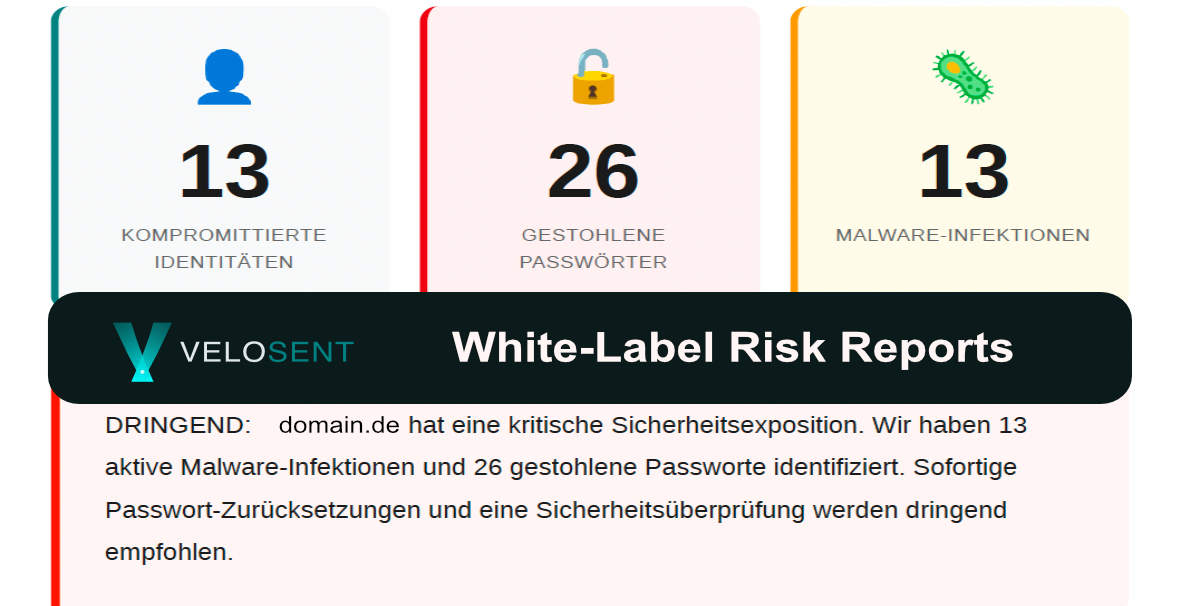
- Velosent creates branded risk reports in under 60 seconds – no subscription required
The Scenario Every MSP Knows
You're sitting across from a small business owner. You've prepared thoroughly, passionately explaining the need for EDR, MFA, and 24/7 monitoring. You know with 100% certainty that their network is wide open.
But at the end, you hear the sentence every Micro-MSP dreads:
"We're too small to be hacked. Besides, nothing has ever happened."
You leave the meeting feeling like you've been talking to a wall. Why don't these customers understand?
Science says: The problem isn't your customers' intelligence. The problem is that you're trying to sell "nothing."
The Problem: Your Product is Invisible
When you do your job as a security provider perfectly, the customer experiences: nothing. No ransomware screen, no data breach, no downtime.
The human brain is evolutionarily trained to evaluate tangible stimuli. For a layperson's brain, the absence of catastrophe is not a product worth paying for.
What is the Tangibility Bias? The Tangibility Bias describes the human tendency to value visible and tangible products higher than invisible services. We'd rather spend €50,000 on a visible company car than €500 on an invisible firewall.
As long as you only explain security ("Tell"), you're fighting against millions of years of instinct. To win, you need to change strategy: "Show, Don't Tell".
The 3 Psychological Barriers in IT Security Sales
| Barrier | The Problem | The Solution |
|---|---|---|
| Optimism Bias | Customers automatically place themselves in the "safe majority" | Personalized evidence shows: The risk affects YOU |
| Curse of Knowledge | Technicians speak "tap codes" instead of melodies | Visual dashboards with traffic light system (Red/Yellow/Green) |
| Present Bias | Immediate costs outweigh abstract future risks | Show existing damage, not prevention |
Barrier 1: The Optimism Bias (The Illusion of Invulnerability)
The Science: People systematically overestimate the probability of positive outcomes. When a CEO hears that "43% of all cyberattacks target SMBs," their brain processes this information selectively. They automatically place themselves in the "safe majority" (the other 57%).
The Solution: Personalized Evidence
You cannot argue this bias away. You must break through it. A generic chart about cybercrime achieves nothing. But a Dark Web Report showing the customer their own password in plain text bypasses the optimism filter immediately.
The customer can no longer think: "That only happens to others." The proof is on the table:
– personalized for your customer
Barrier 2: The Curse of Knowledge (Why Technicians Often Sell Poorly)
The Science: In a famous Stanford study, subjects ("Tappers") tapped the rhythm of well-known songs on a table. Listeners were supposed to guess the songs.
- The Tappers thought 50% of songs would be recognized.
- Reality: Only 2.5% were recognized.
This is the Curse of Knowledge. You are the Tapper. When you speak of "Zero Trust," "latency," and "endpoints," you hear the melody of security. Your customer hears only confusing tapping.
The Solution: Visual Translation
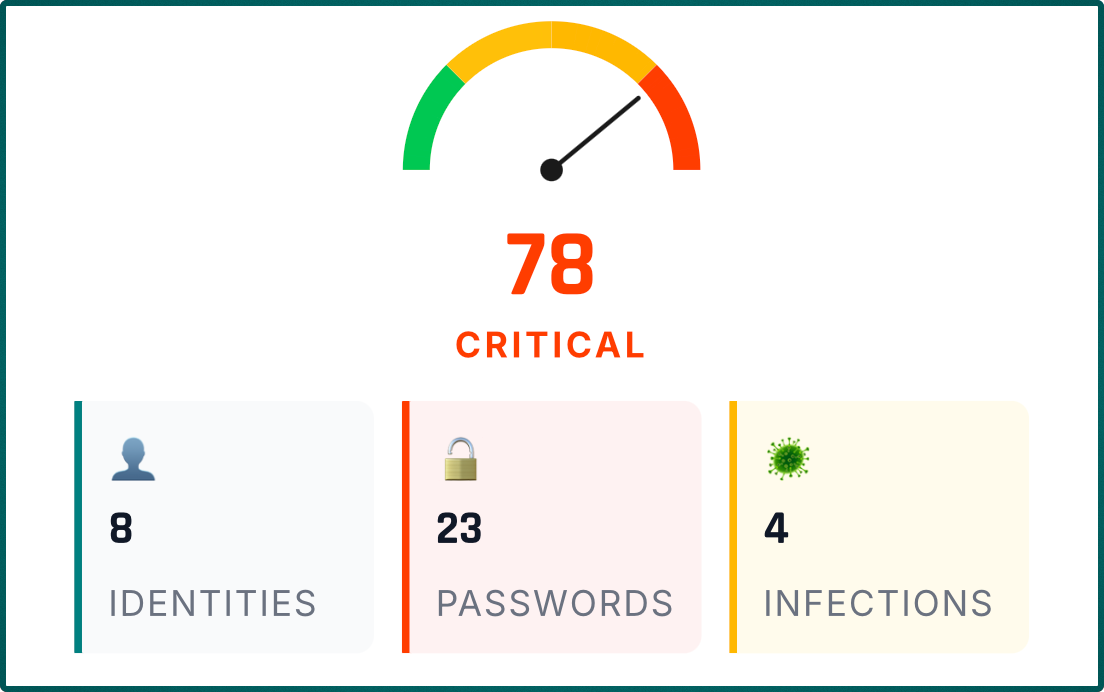
The brain processes images 60,000 times faster than text. Use dashboards with traffic light systems:
Every business owner understands this in 3 seconds, without an IT degree.
Barrier 3: The Present Bias (Why Budgets Are Always Tight)
The Science: People value immediate costs (the MSP's monthly invoice) much higher than abstract future benefits (no hack in 2 years). The pain of payment is now. The fear of a hack is far away.
The Solution: Bring the Pain Forward
Don't show the customer what you will do (prevention), but what has already gone wrong.
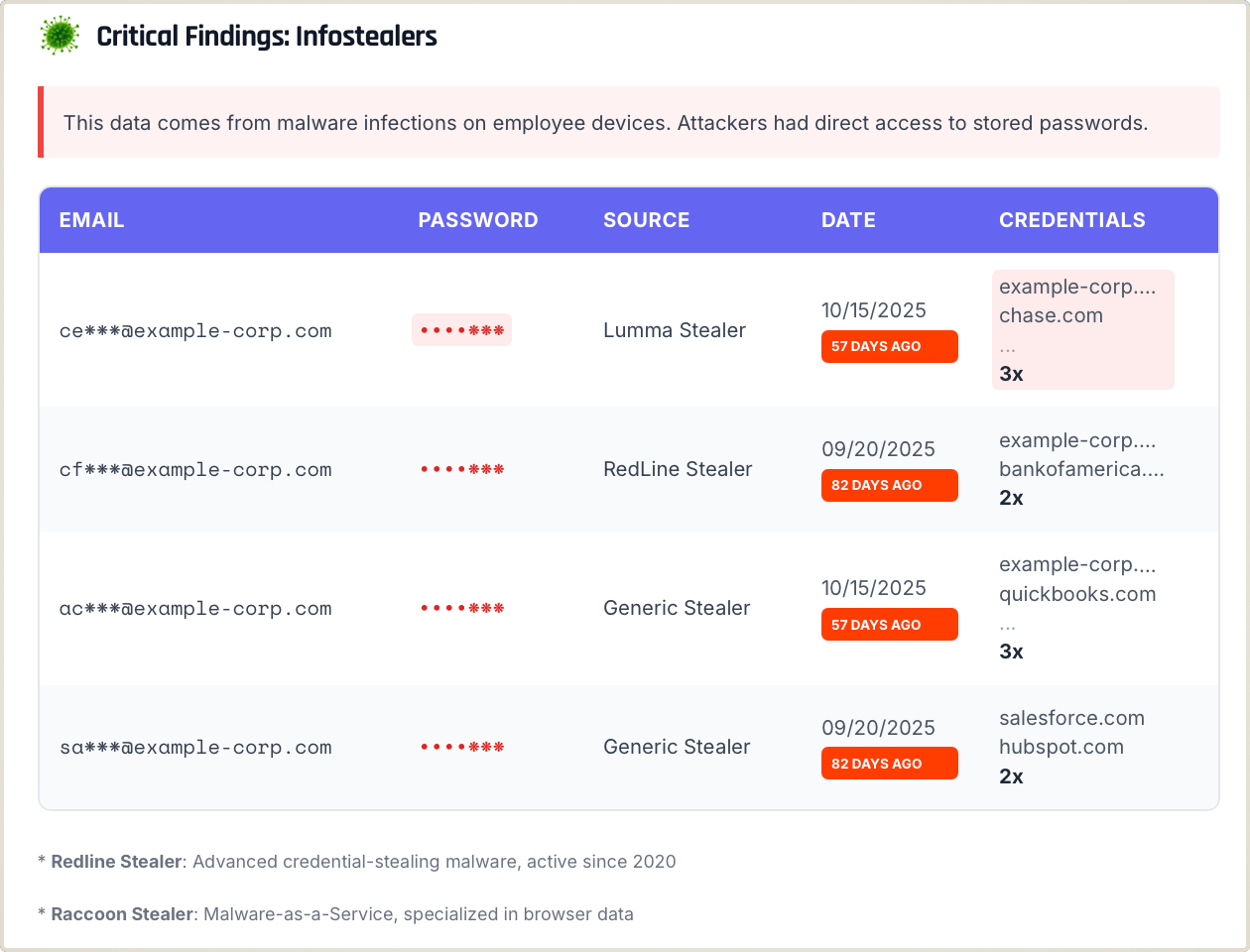
When you present a report that flags an active infection (like the one below), the conversation shifts instantly. It's no longer about buying "insurance" for the future—it's about stopping the bleeding today.
Suddenly, the budget is no longer an issue.
Conclusion: From Supplicant to Eye-Opener
You don't need to be a "sales guru" to sell IT security. In fact, your expertise often prevents you from reaching customers emotionally.
The most successful Micro-MSPs stopped persuading. They started showing.
- Instead of "You need better passwords" → they show a list of compromised logins
- Instead of "We need to patch" → they show a red dashboard
When you make the invisible visible, you're no longer selling "insurance." You're selling the solution to a problem the customer can no longer ignore.
Making the Invisible Visible
Velosent was built exactly for this: Create a branded risk report in under 60 seconds that visually proves to your customers where they stand.
Benefits for MSPs:
- Pay-per-report with no fixed costs – ideal for solopreneurs
- White-label PDF reports with your logo
- GDPR-compliant using public OSINT data
Frequently Asked Questions
What is the Tangibility Bias?
The Tangibility Bias describes the human tendency to value tangible and visible products higher than invisible services. In the IT security context, this means: Customers would rather spend money on visible hardware than on invisible protection against cyberattacks.
How does "Show Don't Tell" work in IT sales?
"Show Don't Tell" means showing the customer concrete visual evidence instead of abstract explanations. A Dark Web scan that reveals the customer's compromised passwords is more convincing than any presentation about cyber risks.
How much does a Dark Web Scan cost for MSPs?
At Velosent, scans start at €9 per report in the pay-per-report model. For growing MSPs, there's a flat rate from €29/month for unlimited reports. There are no minimum contract terms or hidden costs.
Is scanning third-party domains legal?
Yes. Velosent exclusively aggregates data that is already publicly available on the Dark Web (OSINT). No penetration tests are conducted. This falls under Recital 49 of GDPR (network security) as a legitimate interest.